Automated Penetration Testing:
Accurate, Risk-Free, and Continuous
See how attackers move through your environment and prioritize mitigation efforts where they make the biggest impact.
Traditional automated penetration testing tools are known for generating noise—large volumes of vulnerability reports that lack actionable insights. Teams are left to navigate issues like system crashes, network outages, and lists of vulnerabilities without any context. The result? Time wasted on problems that don’t matter, while critical gaps are left open.
While automated pentesting provides broad coverage, it lacks the precision to focus on exploitable vulnerabilities. It tells you where issues exist but doesn’t show how attackers could leverage them to move laterally or escalate privileges.
What makes Picus unique?
We combine the broad reach of automated penetration testing with the precision of attack path mapping, giving you a comprehensive view of your security posture. With clear, actionable results, you can address vulnerabilities efficiently and effectively—saving time, reducing effort, and strengthening your defenses.
Benefits of Picus Automated Penetration Testing
Picus Approach to Automated Pentesting & Attack Path Mapping
Automated penetration testing to uncover critical vulnerabilities coupled with attack path mapping to visualize risks without disruption.
-1.png?width=2000&name=APVhero%20(1)-1.png)
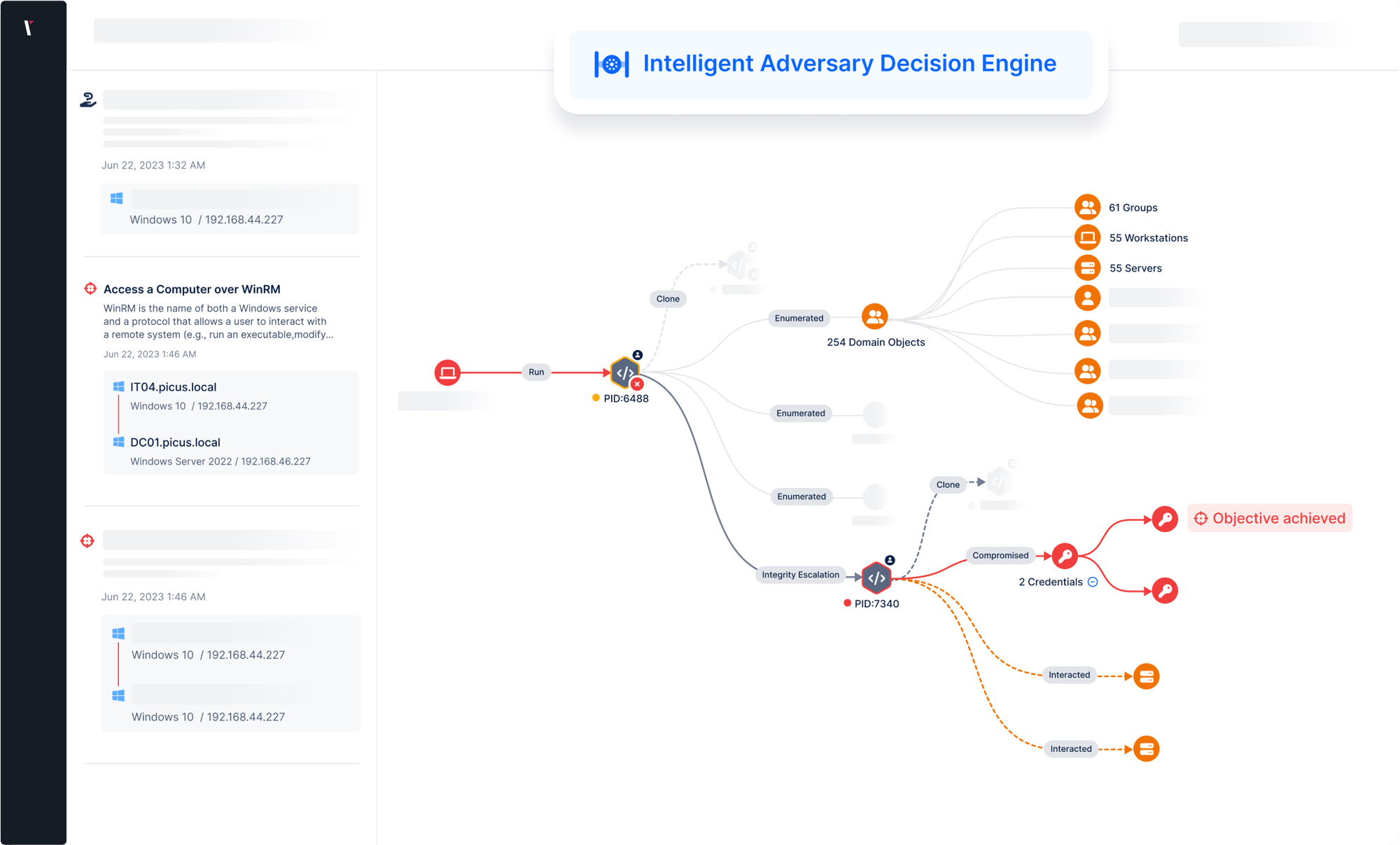
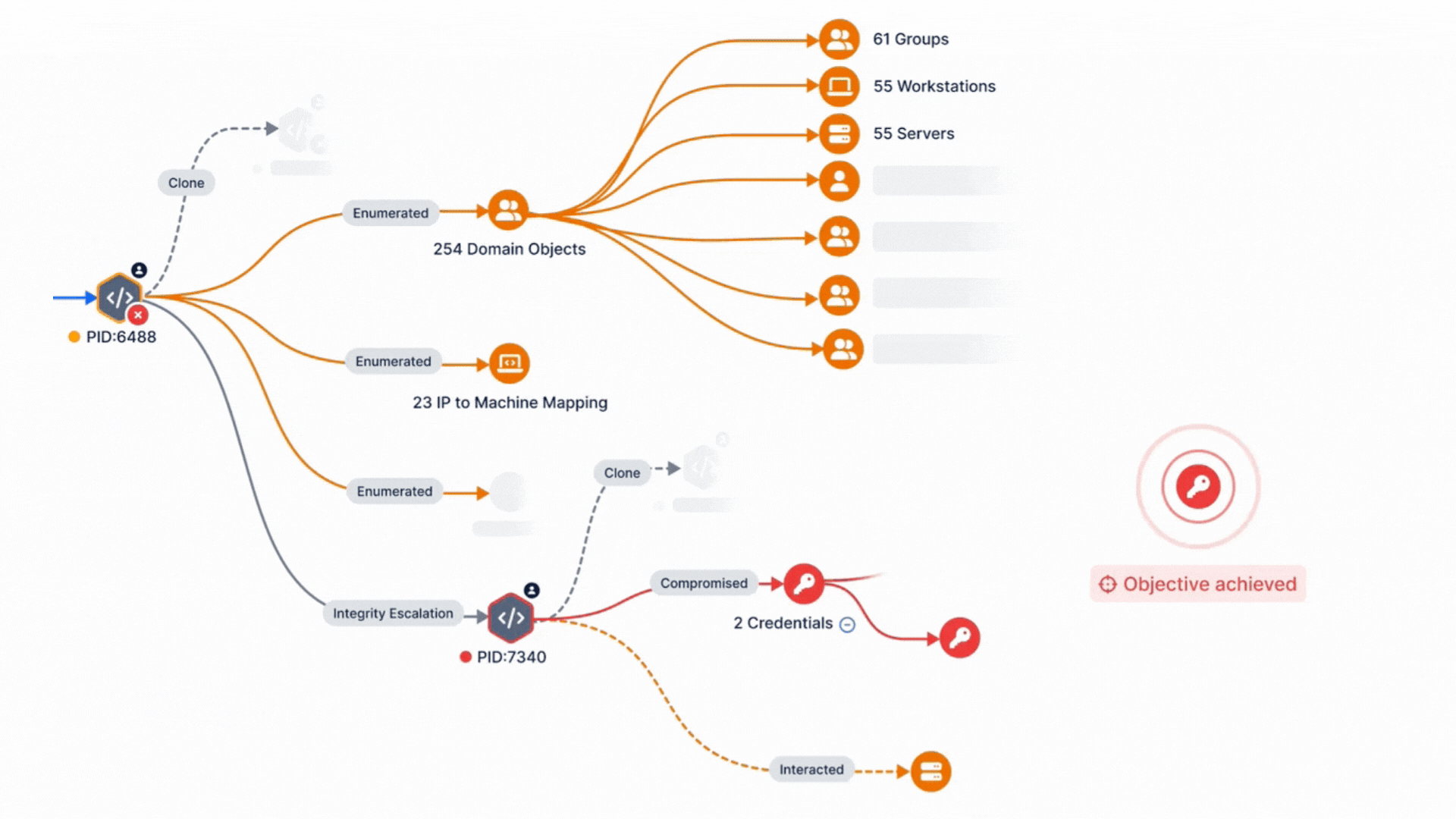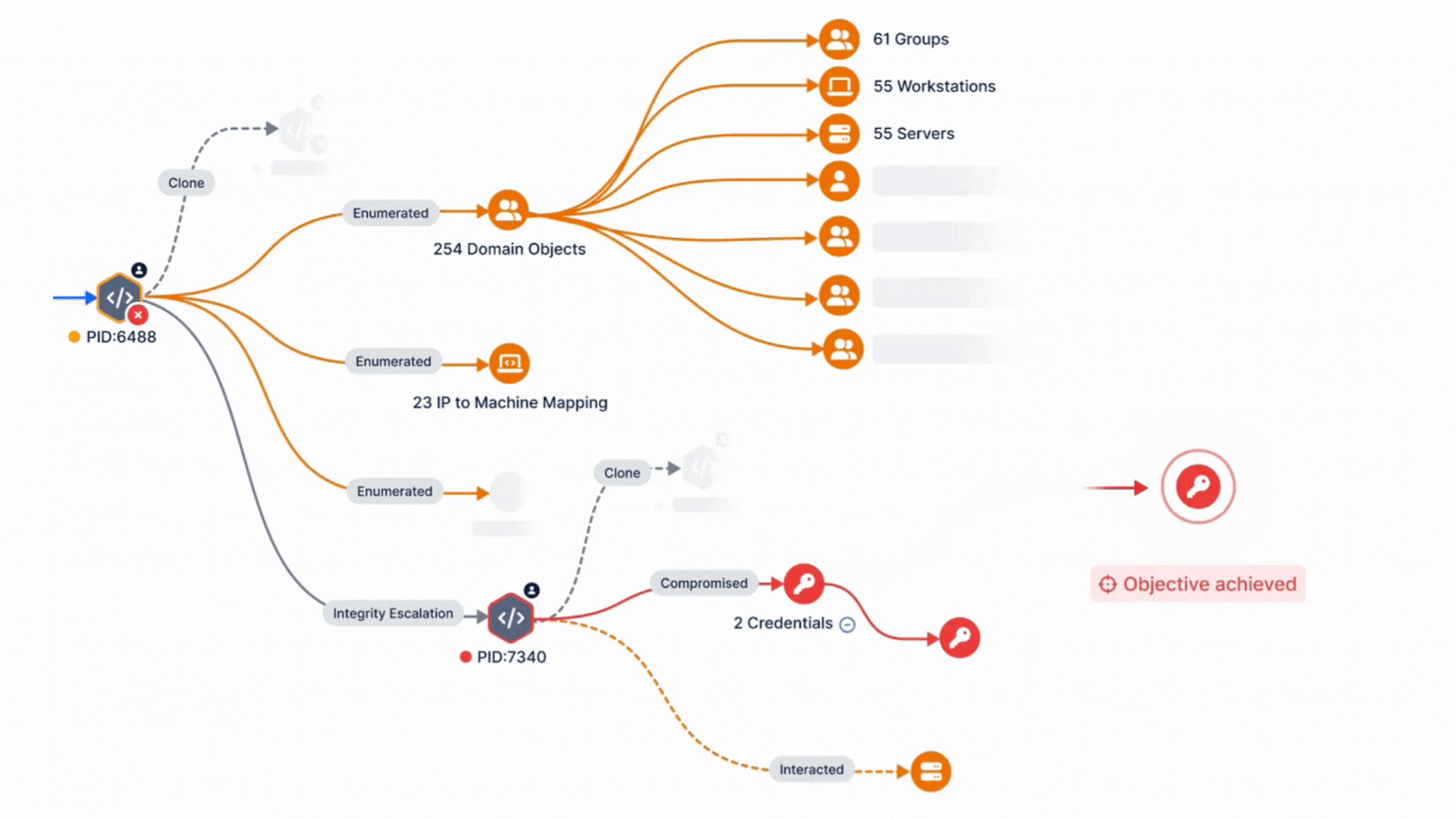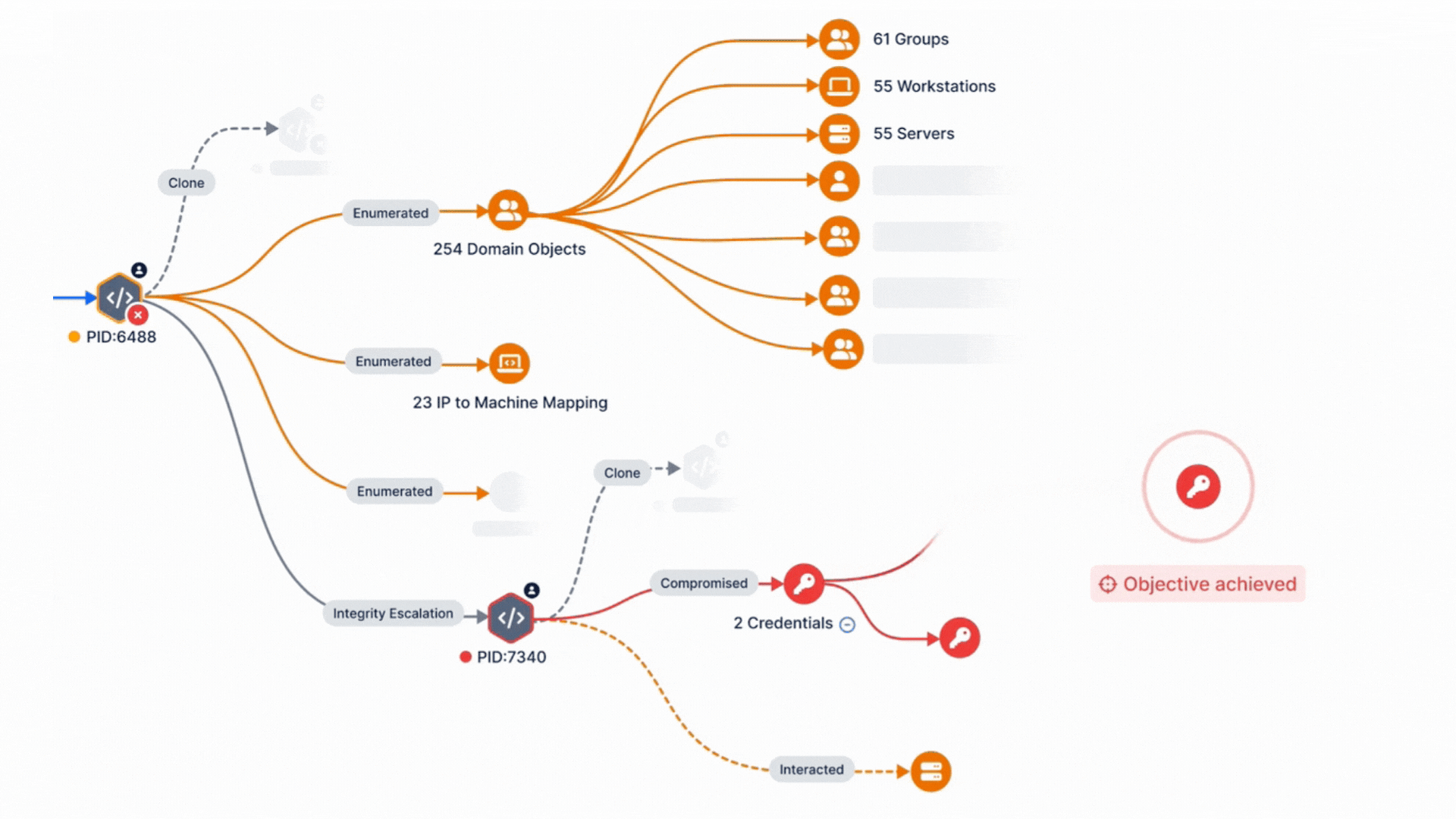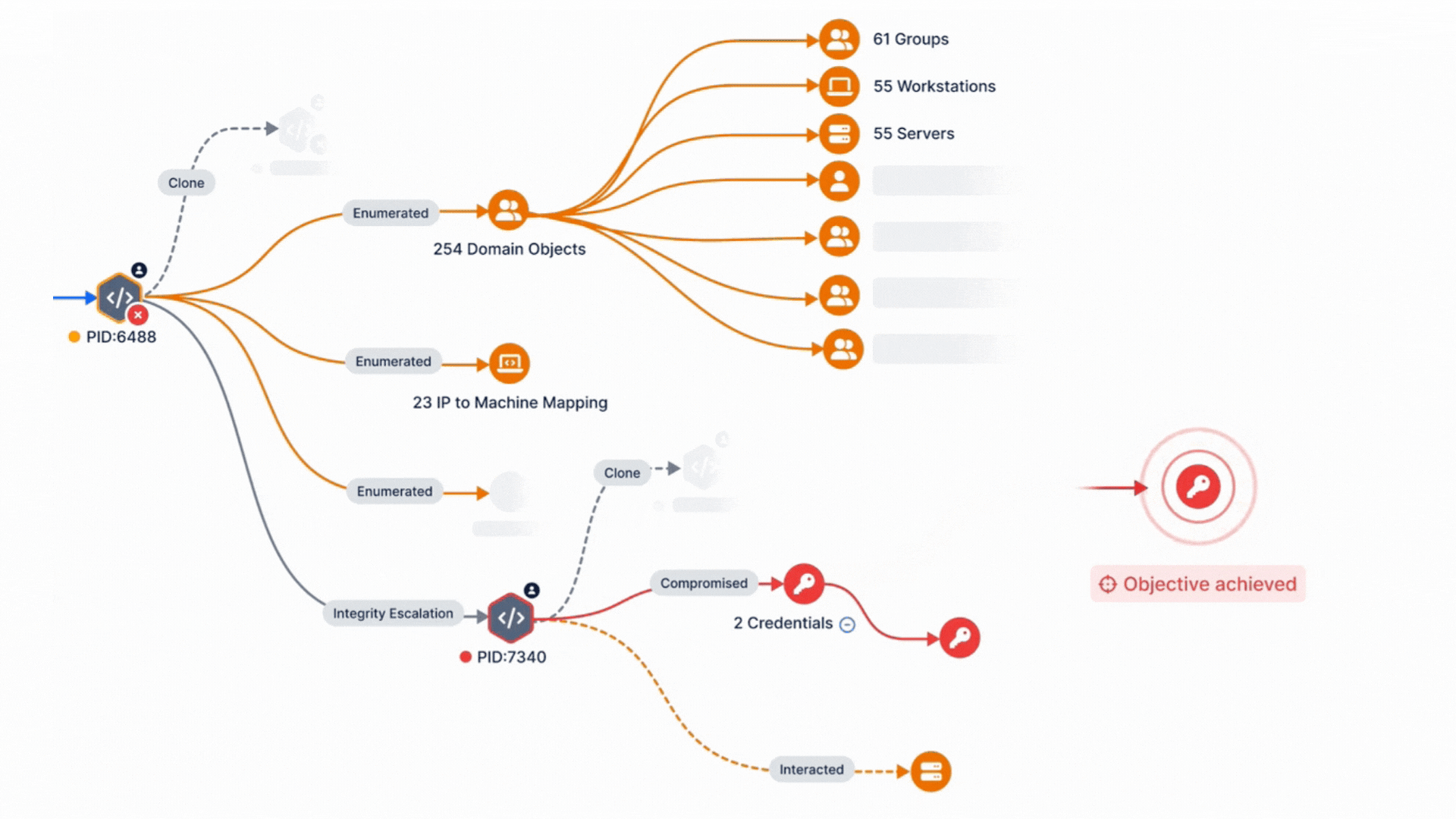
Visualize high-risk attack paths and see how attackers could leverage vulnerabilities and misconfigurations to compromise servers, workstations, and users to achieve their goals, such as gaining domain admin privileges.
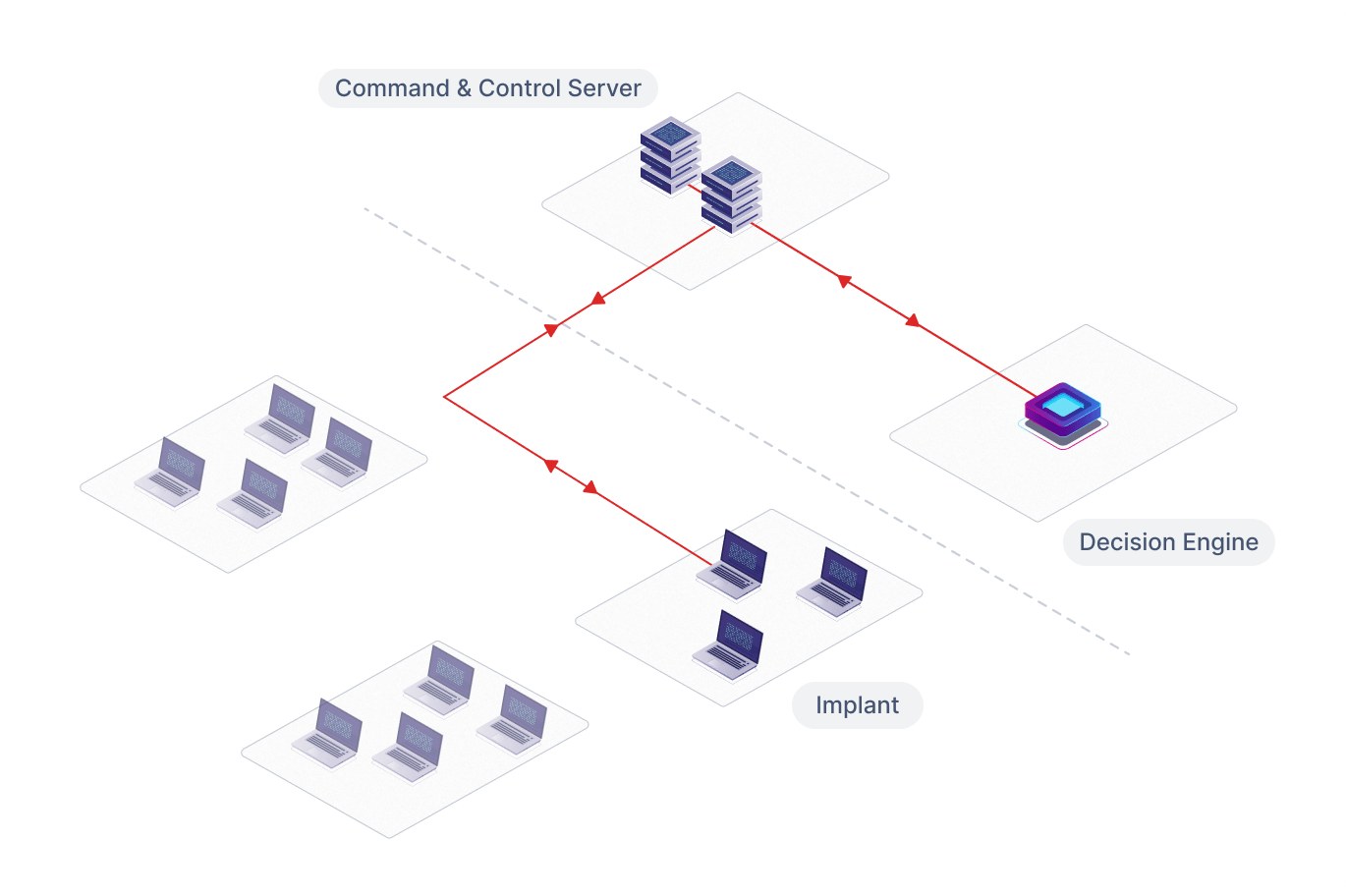
APV is powered by an intelligent decision engine that replicates the approach of real attackers. It determines how the assessment objective can be achieved in the most efficient and evasive way possible.
Benefit from automated pentesting, which broadly tests your security posture like “fishing with a net,” and attack path mapping, which focuses on specific attack vectors like "fishing with a spear.” When used together, these approaches provide a comprehensive security strategy.
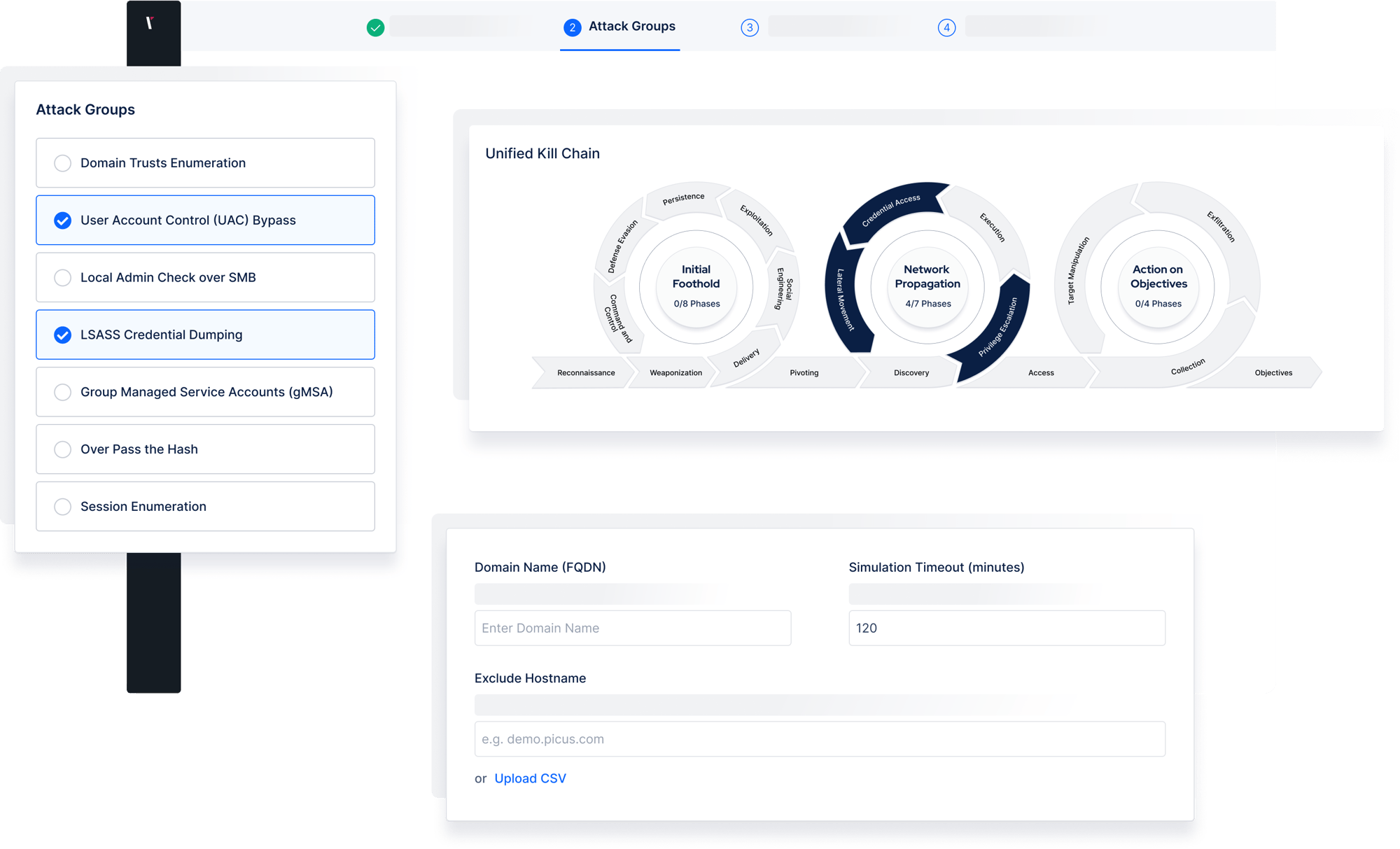
Discover attack paths that are currently open to threat actors, all mapped to the unified kill chain. Combining Breach and Attack Simulation with Automated Penetration Testing allows you to address the highest-risk exposures more efficiently.

Why Security Leaders Choose Picus
Picus Attack Path Validation is the only solution providing a continuous, risk-free, and accurate approach to automated penetration testing and attack path mapping.
Picus Security
Alternatives
OUR CustomerS SAY
Picus APV has been instrumental in elevating our proactive defense capabilities, particularly through its automated penetration testing features.
Its capabilities allow us to identify gaps swiftly and enhance our cybersecurity posture in real-time.

REQUEST DEMO
See Picus in Action
Fill out the form to request a demo or speak to our team to get answers to any questions.


