Breach and Attack Simulation for Confident Decisions
Validate real attack behavior across your environment and prioritize action with clear outcomes.
Why Teams Choose Breach and Attack Simulation
Security teams don’t struggle because they lack the tools. They struggle because everything looks critical.
Breach and attack simulation tells you:
-
What is exploitable right now
-
What actually bypasses your defenses
-
What deserves attention today
That shift removes noise, reduces decision fatigue, and restores confidence.
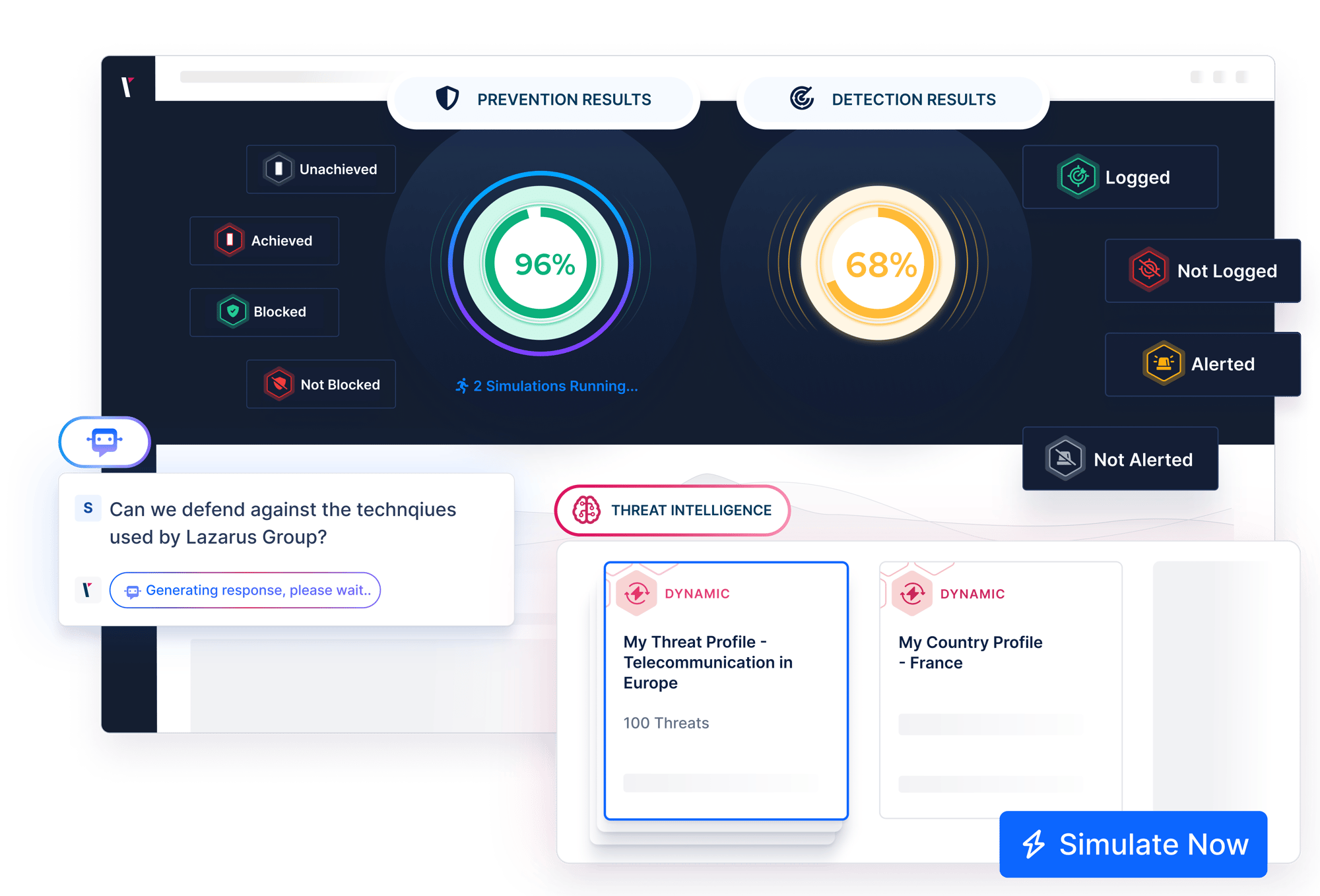
How BAS Works: Evidence-Based Security Validation
Designed to remove uncertainty by proving which security controls actually stop real-world attacks. Validation runs continuously without manual effort.

Key Features of an Effective BAS Solution
Breach and Attack Simulation should simplify security operations by validating what is at risk and replacing guesswork with evidence.
What Security Teams Gain from BAS

Why Security Leaders Choose Picus BAS
.png?width=1267&height=1000&name=An%20extensive%20library%20of%20real-world%20threats%20(2).png)
.webp?width=1292&height=1000&name=Mitigate%20and%20optimize%20before%20a%20breach%20(2).webp)
Premium Threat Library
Vendor-Specific Mitigations
With vendor-specific mitigation, you can apply precise fixes and saving remediation time.
.png?width=1257&height=1000&name=Executive%20reports%20and%20dashboardsand%20(2).png)

Security Posture Tracking
Response to Emerging Threats

Individually Licensable Attack Modules
Test your controls against a regularly maintained attack library, comprising thousands of real-world threats and attack actions.
Validate that malware and ransomware, downloaded via client-side attacks, is prevented and detected.
Test the effectiveness of your controls to block malicious links and attachments.
Gauge if your defenses are capable of blocking code injection, denial of service and brute force attacks.
Validate that scenario attacks by threat groups, including APTs, are identified by endpoint security controls.
Assess whether your defenses can prevent the exfiltration of sensitive personal and financial information.
10 Criteria for Choosing the Right BAS Solution

Frequently Asked Questions
When evaluating a BAS solution, you need to consider the following criteria.
Up-to-date Against Current and Emerging Threats:
An effective BAS solution must remain updated to address both current and emerging threats. As the cyber threat landscape continually evolves, the threat library in BAS should be consistently refreshed to keep pace with new techniques, vulnerabilities, and attack campaigns.
Threat Simulation Across the Full Attack Lifecycle:
An effective BAS solution should simulate a range of cyber threat techniques spanning the entire attack lifecycle. This includes:
- Pre-Compromise Attacks: Email-based threats, malware downloads, vulnerability exploitations, and web application attacks.
- Post-Compromise Attacks: Endpoint-specific attacks, data exfiltration, and lateral movement within the network.
- Attack Campaigns: Scenarios based on malware tactics and campaigns led by known threat groups.
Threat Customization:
Every organization faces a unique cyber threat landscape, necessitating tailored threat prioritization. BAS should provide threat profiling to assist SOC teams in identifying and prioritizing relevant risks. Additionally, it should allow custom attack simulations and campaigns, enabling security teams to simulate their specific threat landscape and accurately assess their security posture.
Direct and Actionable Mitigation Insights:
Threat simulations reveal gaps in security controls, and a BAS solution should provide actionable mitigation guidance for these gaps, including emerging threats and zero-day vulnerabilities (when a public PoC is available). This empowers SOC teams to quickly craft tailored mitigation strategies.
Real-Time and Customized Reporting:
BAS solutions should generate assessment reports suitable for various stakeholders, including executives, SOC teams, and auditors. These reports should present real-time metrics, such as overall security score, detection rate, log collection, detection, and prevention.
Mapping to MITRE ATT&CK and Other Frameworks:
A robust BAS solution should support industry frameworks like MITRE ATT&CK, mapping threat simulations to standardized methodologies. This alignment helps organizations identify security gaps, benchmark against industry best practices, and prioritize remediation based on the most relevant threats.
Ease of Use and Ease of Deployment:
A BAS solution should be easy to deploy and use to ensure seamless integration with an organization's existing security infrastructure. The solution should have a user-friendly interface and provide clear instructions for deployment, configuration, and maintenance. Additionally, it should offer flexible deployment options, such as on-premises, cloud-based, or hybrid, to accommodate different organizational needs and network architectures. An easy-to-use and easy-to-deploy solution will encourage adoption and help organizations maximize the benefits of a BAS solution.
There are three main benefits of a BAS solution.
Continuous Validation of Cyber Risk Factoring Security Control Effectiveness
BAS solutions offer substantial advantages over traditional security practices such as manual penetration testing and red teaming. Traditional methods, while effective, are often constrained by the need for skilled professionals, limited scope, resource demands, and variability in outcomes. Additionally, they are typically conducted only once or twice a year due to high costs and potential disruption to organizational networks and resources. This limited frequency prevents them from effectively validating newly emerging exposures between engagements.
As attack surfaces continue to expand and become increasingly dynamic, the continuous assessments provided by BAS solutions are essential. BAS delivers automated, ongoing stress testing on an organization’s security controls against the latest and most sophisticated adversarial behaviors, offering a more adaptive and resilient approach to managing today’s complex security landscape.
Better Mobilization of Remediation Efforts with BAS
One of the benefits of BAS tools, as highlighted earlier, is their ability to reduce the sheer number of exposures, filtering them into a manageable set for the security team to address. Although Exposure Assessment Platforms (EAPs) can identify hundreds or even thousands of exposures, it is impractical for any security team, regardless of size, to tackle every single issue. Additionally, being required to address each identified exposure can significantly disrupt business operations, as patching and remediation efforts take time and can put operations on hold.
To address this, BAS solutions validate identified exposures to determine which ones are feasible for an adversary to exploit within an organization’s IT environment. This approach effectively bridges the prioritization gap left by legacy scoring systems like CVSS and EPSS. While these systems are useful for indicating the maximum potential impact of, for example, a CVE, adversarial exposure validation tools like BAS reveal the true impact of a specific exposure within the organization.
In other words, BAS helps security teams understand whether an attempted attack leveraging a particular CVE can be blocked immediately, partially, or, if not, at least logged and alerted as expected. This technique assesses the effectiveness of existing security defenses, sparing the team from addressing theoretical risks with no practical threat to the organization.
As a result, BAS provides a smaller, prioritized subset of exposures for remediation, enabling more efficient resource allocation.
Actionable Results and Mitigation Suggestion for Smooth Remediation
One of the most critical benefits of BAS solutions is the actionable, ready-to-apply mitigation suggestions they offer. BAS tools excel not only in validating which exposures need remediation but also in delivering mitigation recommendations that are researched and tailored for a variety of security control vendors.
This is essential because, in many cases, remediating vulnerabilities can take several days or weeks and may disrupt business operations. To address this challenge, BAS tools provide immediate mitigation suggestions that can be applied to security controls, giving security teams valuable time to fully remediate the exposure while minimizing disruptions.
To choose the right breach and attack simulation tool for your organization, evaluate its ability to continuously test security controls, its integration with a diverse range of security controls, and the actionability and relevance of its results and mitigation suggestions to your specific security needs.
Consider using breach and attack simulation tools when you need continuous and automated security assessments to stay ahead of evolving cyber threats and to ensure security controls are effective against real-world attack scenarios.
BAS platforms test and validate the performance of security controls, including but not limited to:
- Next-Generation Firewalls (NGFW)
- Intrusion Detection Systems (IDS)
- Intrusion Prevention Systems (IPS)
- Anti-virus and Anti-malware Software
- Endpoint Detection and Response (EDR)
- Extended Detection and Response (XDR)
- Data Leakage Prevention (DLP)
- Security Information and Event Management (SIEM) solutions
- Email Gateways
To learn more, please visit Integrations and Supported Technologies page.










![The Saudi Investment Bank [SAIB] logo (1)](https://insights.picussecurity.com/hs-fs/hubfs/The%20Saudi%20Investment%20Bank%20%5BSAIB%5D%20logo%20(1).png?width=416&height=121&name=The%20Saudi%20Investment%20Bank%20%5BSAIB%5D%20logo%20(1).png)
.png?width=369&height=133&name=Government%20Technology%20Agency%20of%20Singapore%20logo%20(1).png)

