CTEM
Implement Continuous Threat Exposure Management Program
Reduce your threat exposure by 50% in less than three months.
Prioritize and address critical risks swiftly.
Address Critical Exposures Fast
Adopt CTEM with Picus. Integrate and validate across endpoints, networks, and cloud environments to determine your business's critical areas.
.png?width=2000&name=Visuals02%20(1).png)
.webp?width=2000&name=Mitigate%20and%20optimize%20before%20a%20breach%20(2).webp)
Integrate with various technologies and validate endpoints, network technologies, security controls, and cloud environments.
Align your CTEM program with business priorities for effective scope definition.
Visualize assets and vulnerabilities based on their risk level and prioritize them to achieve effective threat exposure management across your environments.
Gain a unified view of your infrastructure with data from over 50 integrations.
Aggregate, curate, and analyze exposures. Focus on high-impact attack paths and chokepoints to allocate resources efficiently.
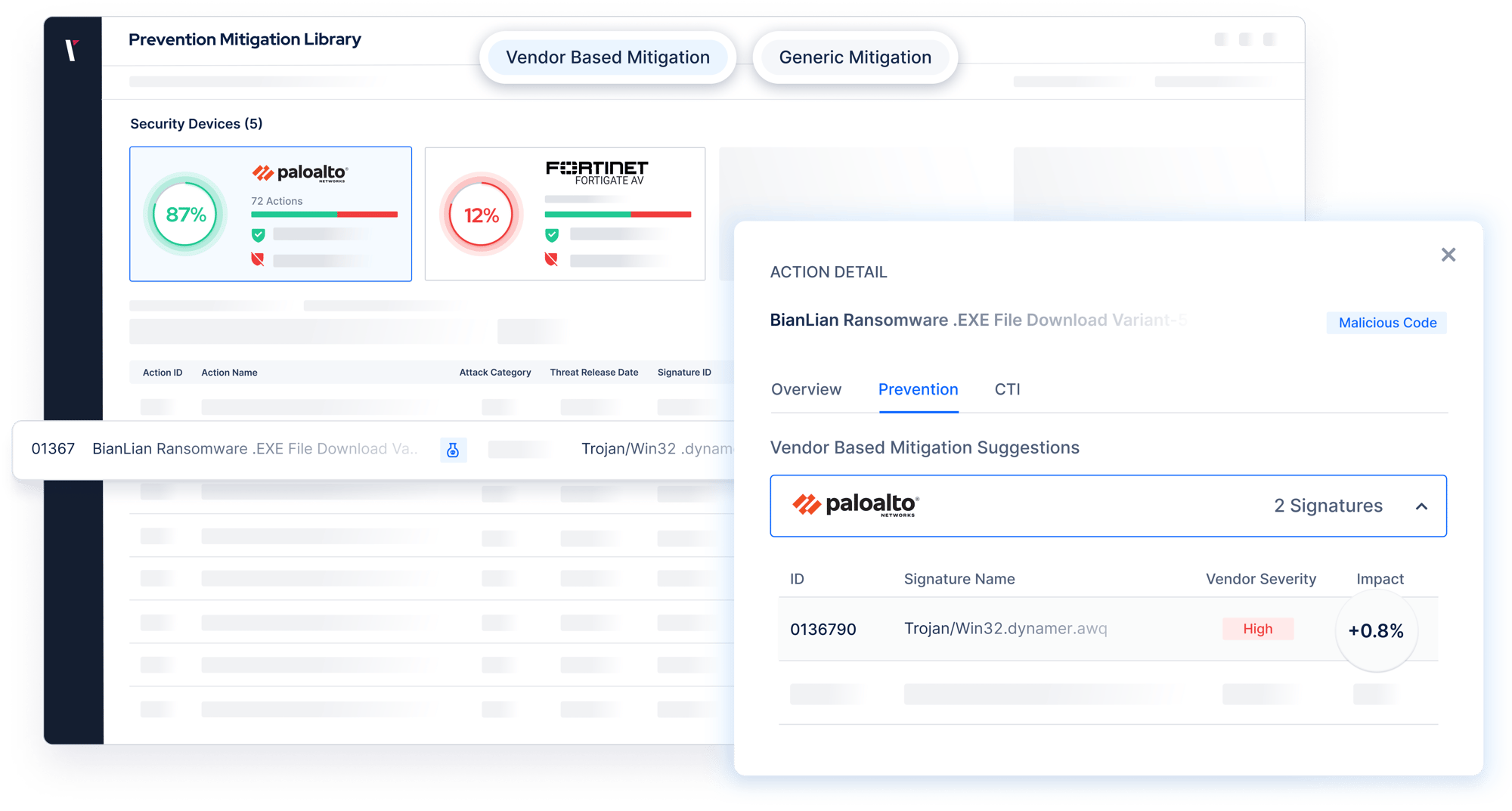
Get actionable mitigation strategies for each exposure and choke point.
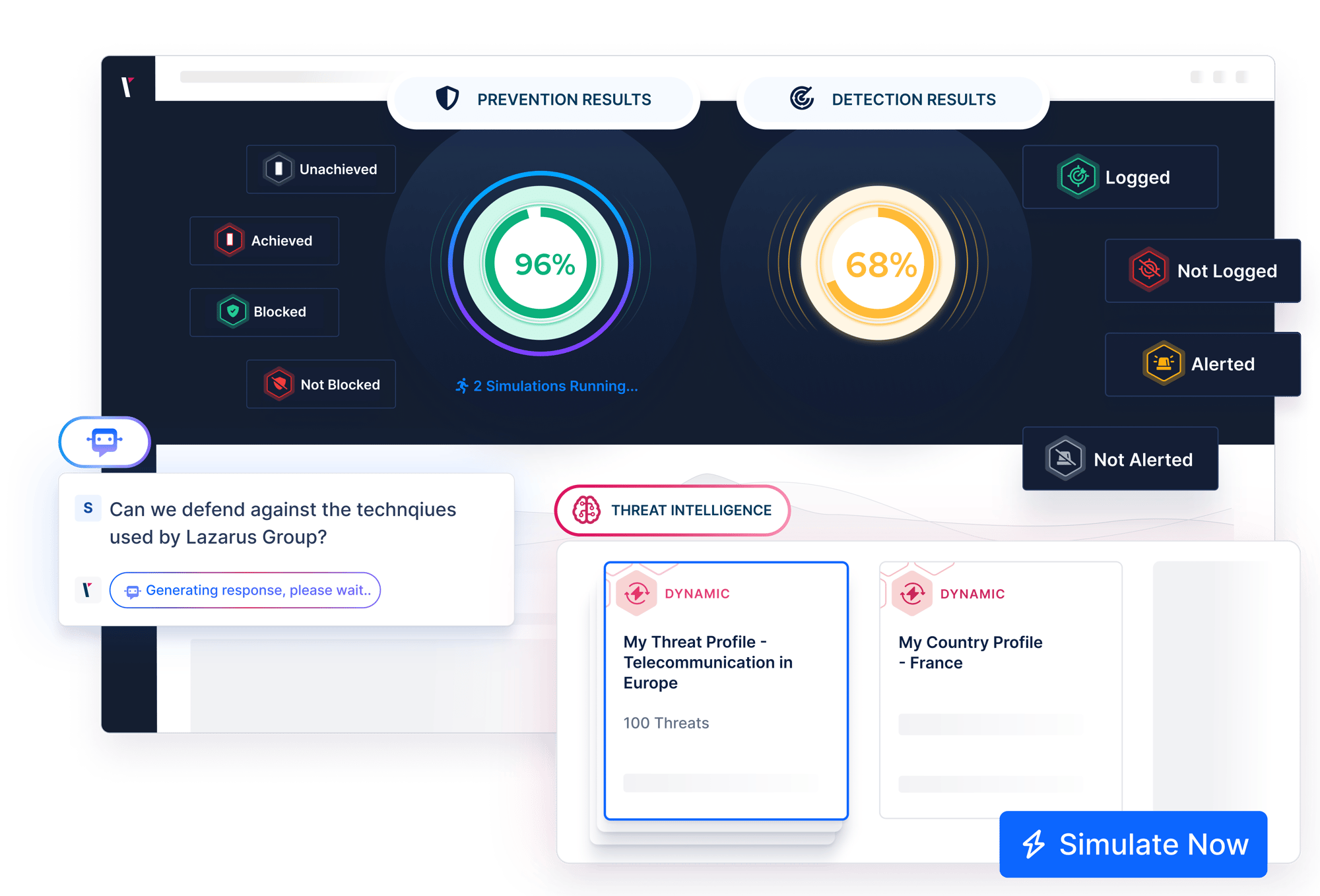
Consistently measure the effectiveness of your security controls with accurate attack simulations.
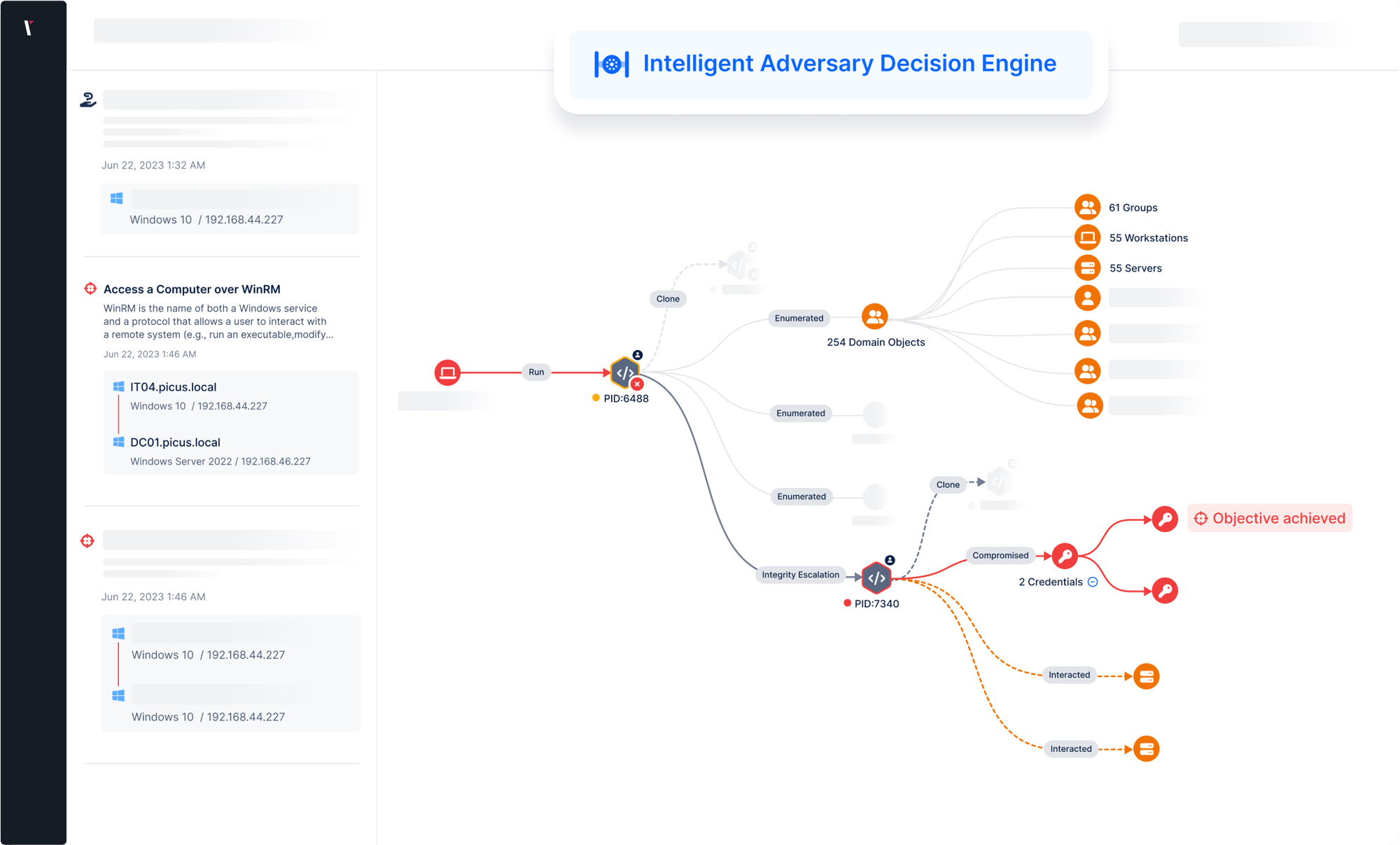
Find the possibility of threat actors' pivoting and lateral movement between internal hosts.
Before proceeding to the mobilization step, determine whether your prevention and detection controls are configured to provide the coverage and visibility you need.
Implement actionable mitigation strategies quickly.
Using Picus's vendor-specific mitigation recommendations, patch exposures, harden infrastructure, or deploy preventive and detective security controls to remediate prioritized exposures.
Why Choose Picus for Your CTEM Program?
Our Customers Adopted CTEM Effortlessly

“The Picus Platform helps us efficiently manage diverse security products and understand our readiness against the latest threats”

“The Picus Platform has strengthened our security and revolutionized our security operations, resulting in significant time and cost savings. It's now the cornerstone of our cybersecurity strategy.”

“Since implementing The Picus Platform, we have witnessed a 23% increase in our prevention security score. This improvement reflects our strengthened security posture and our ability to protect critical assets."
The State of Threat Exposure Management

