Reduce Exploitable Exposures
CTEM Needs More Than Visibility
Visibility without validation is just another to-do list for security teams. You need to know what’s critical, what’s exploitable, and what to fix first. Validating and fixing the right risks, fast, is how you stay ahead of attackers.
That means answering questions your VM tools can’t:
- Which exposures are exploitable in your environment?
- Which ones can attackers chain to reach your crown jewels?
- Are your controls stopping critical threats?
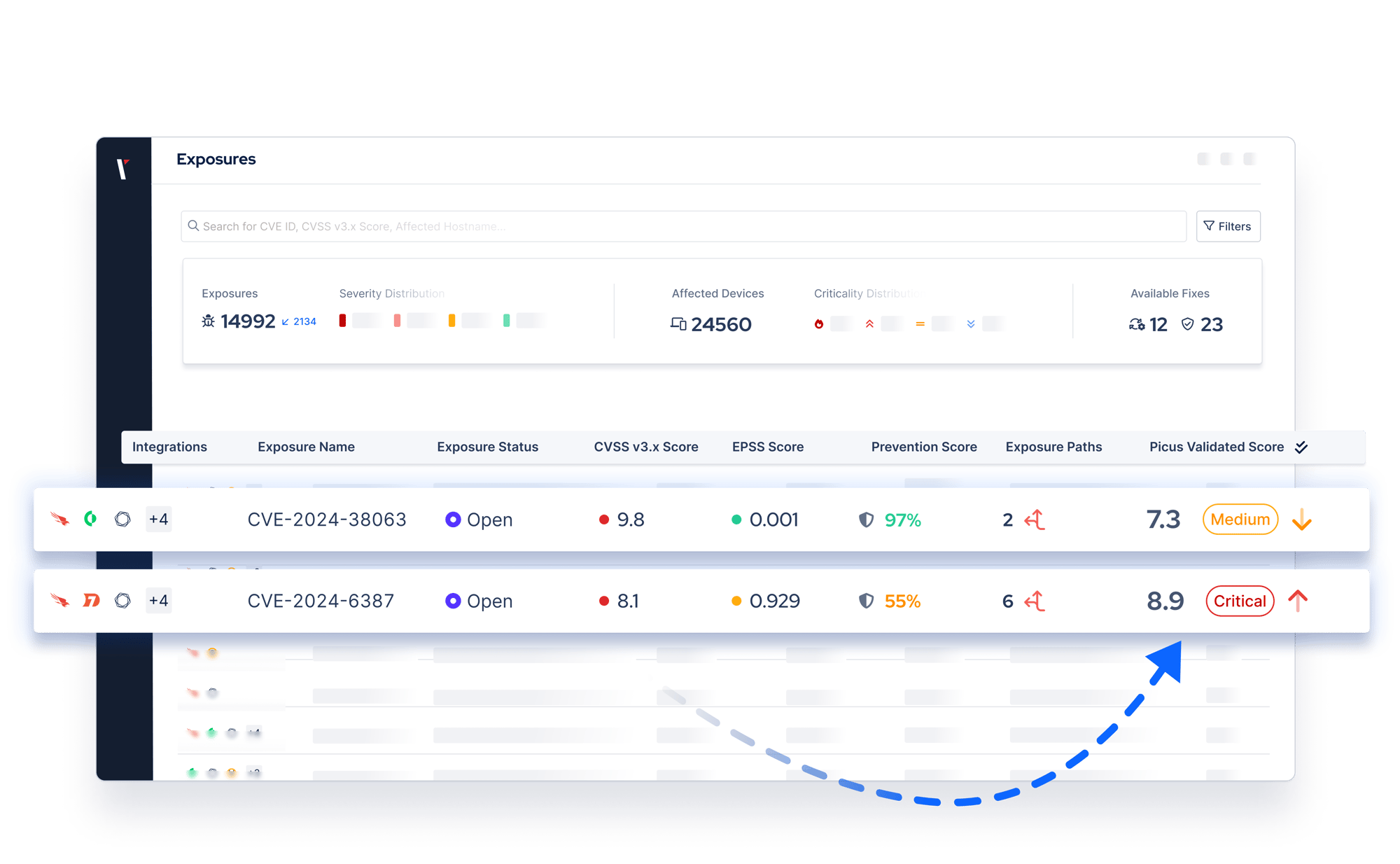
Expose Which Attacks Can Breach Your Defenses
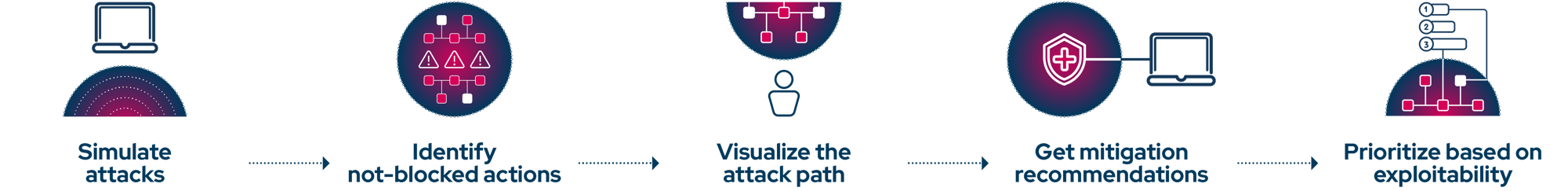
Picus simulates the entire chain, from initial access to privilege escalation, and delivers detailed findings at every step. You see which controls stop the attack and which gaps remain.



Expose Which Attacks Can Breach Your Defenses
Picus simulates the entire chain, from initial access to privilege escalation, and delivers detailed findings at every step. You see which controls stop the attack and which gaps remain.
Key Capabilities
Picus helps you stop real threats, not just dozens of scary-sounding bugs. You only focus on vulnerabilities that can have an actual impact, so your team isn’t overwhelmed trying to fix everything.




How Picus Fits Into CTEM
Scoping
Discovery
Extend visibility beyond CVEs. Picus discovers misconfigurations, insecure services, and hidden assets, then maps how they connect to critical targets.
Prioritization
Validation
Mobilization
request demo
Get Your CTEM Demo
CTEM is a process. Picus Platform makes it easier.
Discover how Picus can help you prevent twice as many threats within 3 months.












.png?width=353&height=200&name=Picus-BlueReport2025-Preview2-HubPage%20(2).png)