Automated Security Validation
Consistently validate your security to measure your cyber risk and be more confident in your defense.
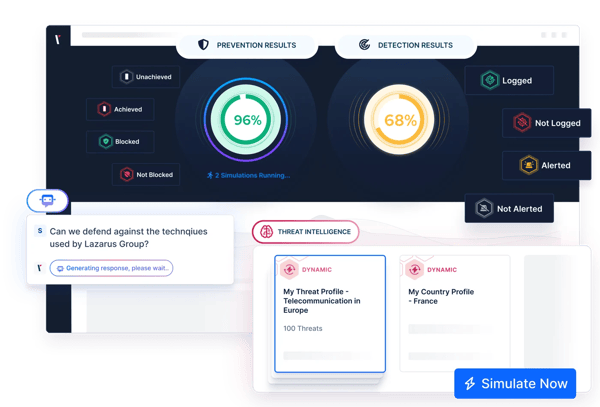
Security Validation is a comprehensive process that includes assessment, validation, and prioritization to harden your cybersecurity posture.
By regularly assessing, testing your security controls, and surfacing exploitable attack paths before bad actors - you can strengthen prevention and detection efforts.
The Picus Security Validation Platform reduces your cyber risk by accurately measuring your exposure to cyber threats with real-world attack simulations.
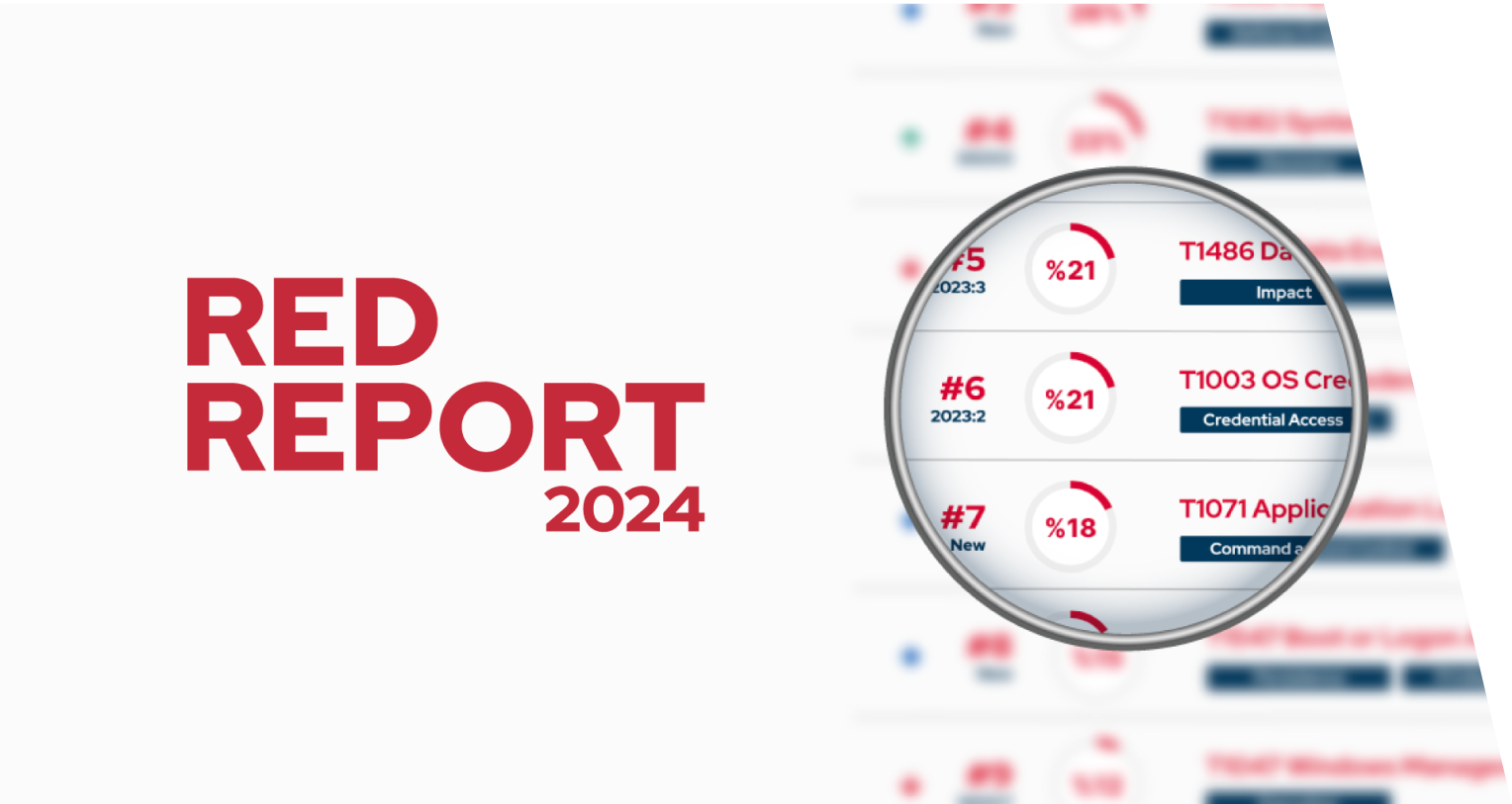
The Red Report 2024
Discover the ATT&CK techniques commonly used by malware, learn how to defend against evasive ‘Hunter-killer’ variants and see:
- How attacker behaviors continue to evolve
- The 10 most prevalent ATT&CK techniques
- Key strategies to enhance your threat readiness
Get More with Security Validation
-
Attack Simulations: plan and schedule targeted attacks on your systems to test exploitable vulnerabilities and keep controls up to date.
-
Exposure Assessments: see a detailed view of potential security weaknesses, drawing context from your attack surfaces, vulnerabilities, and more.
-
Security Audits: review and optimize the effectiveness of your security controls and policies to ensure that they are effective at preventing and detecting the latest threats.
-
Risk Quantification: measure the effectiveness of your security program to benchmark performance and evidence cyber readiness to key stakeholders.
When to Use Security Validation
Focus on the most critical areas by visualizing gaps and providing data on which threats a particular mitigation measure can block.
Identify gaps in your rules base and ensure that detection rules correctly identify threats.
Enhance log management practices by validating that the necessary logs that detect attacks are being collected.
Why Picus for Security Validation
percent of Gartner® Peer Insights™ reviewers recommend Picus.
organizations and counting trust our platform globally.
threats simulated consistently and accurately.
percent average increase in prevention capability in 3 months.
The Picus Security Validation Platform
.png?width=950&height=443&name=Platform-Visual%20(1).png)
Our value
Interested to learn more about how Picus can validate your security controls?
Request a demo from our security validation experts.
Frequently Asked Questions
Security validation reduces cyber risk by verifying that an organization’s cyber security program is effective at defending its critical assets against the latest threats.
Without consistent validation, security teams can never be confident that security controls and processes are working as expected.
Due to the ever-changing threat landscape and IT infrastructure drift, security validation is a process that must be performed frequently.
Only by performing automated security validation can organizations obtain the insights they need to stay on top of their security posture and proactively identify and respond to risks sooner.
By continuously testing and helping to improve the effectiveness of security controls, the Picus Security Validation Platform helps organizations comply with a wide range of regulations and standards.
Laws such as The General Data Protection Regulation (GDPR) state that organizations should have a process for regularly testing, assessing, and evaluating the effectiveness of technical and organizational measures. ISO-27001 and the PCI DSS and frameworks such as NIST 800-53 also have similar requirements.
Yes, the Picus Security Validation Platform can seamlessly integrate with various security tools and systems within an organization. This integration enables a holistic and efficient approach to security, enhancing visibility and fostering proactive responses to potential threats.