Know the Risk, Stop the Attack
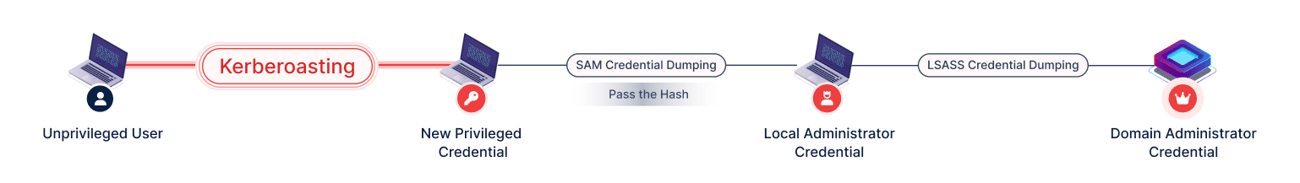
Kerberoasting
Kerberoasting reveals vulnerabilities in your Active Directory, making your organization susceptible to credential theft and privilege escalation.
Watch the product demo to see how you can identify and mitigate these risks.
Know the Risk, Stop the Attack
Kerberoasting
Kerberoasting reveals vulnerabilities in your Active Directory, making your organization susceptible to credential theft and privilege escalation.
To learn more about Kerberoasting, check out our interactive demo below.
Assume Breach
Take Action
Talk to A Red Team Expert
Get insights into Kerberoasting risks in your environment.
Try Yourself
Simulate real adversary behavior with ransomware objective
The Hidden Danger: Kerberoasting
A successful Kerberoasting attack enables attackers to escalate privileges and move laterally across the network, leading to unauthorized access, severe disruptions, reputational damage, and recovery costs potentially running into millions.

of adversary breakout time hits an all time low
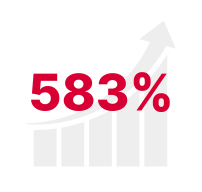
increase in Kerberoasting identity attacks in 2023
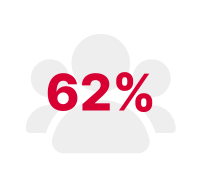
of all interactive intrusions involved the abuse of valid accounts
*CrowdStrike Threat Hunting Report 2023
Kerberoasting Requires More Than Basic Scanning
Targeted Objective-Based Simulations
Go beyond just identifying vulnerabilities that traditional Vulnerability Management tools often miss.
Focus on specific outcomes and impacts on your business.
Comprehensive Attack Path Visualization
Gain clear insight into potential attack paths, prioritizing risks based on real-world impact.
Visualize choke points to understand and mitigate your most significant vulnerabilities.
Full Attack Surface Exploration
Explore and identify all potential attack paths.
By adjusting the initial access point, get a complete view of your attack surface, ensuring a robust defense strategy.
Real-World Actions for Defense-in-Depth
TALK TO A RED TEAM EXPERT
Validate Paths to Critical Assets
Choose a time that works for you to explore how our platform identifies Kerberoastable users and helps protect against advanced threats.
Frequently Asked Questions
Picus Attack Path Validation doesn’t overwhelm security teams by revealing thousands of theoretical paths that are challenging to prioritize. Instead, it simulates the actions of a real-world attacker to discover the shortest path and verify that it poses a genuine risk.
The platform supplies mitigation recommendations for all actions successfully performed during an assessment.
After you schedule a meeting, our technical experts will join the call to understand your specific security needs and concerns. They will guide you through how Kerberoasting can impact your environment, demonstrate how to identify and mitigate these risks and answer any technical questions you may have.
The goal is to provide you with valuable insights tailored to your needs, so you can take informed steps to improve your security posture—without any pressure to commit.
You can begin by clicking here. This will guide you through a setup process where you can simulate a real-world Kerberoasting attack and see how your environment handles the threat.
Picus platform is designed with specific features and functionalities that ensure it does not spread cyberattacks or have a negative impact on your environment. Here are several key reasons why you can be confident that Picus will not cause harm:
No Interaction with Production Assets: Simulating cyber attacks among its agents, the Picus platform operates without any interaction with assets in your production network. This means it doesn't attempt to exploit vulnerabilities or compromise systems during its assessments. Instead, it mimics cyber attacks in a controlled and safe manner, ensuring that your actual production assets remain untouched. This approach ensures that testing does not interfere with actual production systems, preventing any risk of damage or disruption to those systems.
Low Network Load: Picus assessments generate minimal network load, comparable to a user browsing a news website. This means that the network activity generated by Picus is very low and should not disrupt your normal network operations or cause any performance issues. Picus is designed to be non-intrusive in this regard.
Non-Invasive and Non-Destructive Assessment Methodology: The Picus platform is designed to simulate attacks without altering or damaging target systems. It does not attempt to exploit vulnerabilities in a way that could lead to data loss, system crashes, or any other negative impacts. This approach rules out the possibility of data corruption, system instability, or inadvertent triggering of real security incidents, thereby safeguarding the integrity of your systems.
Customizable and Controlled Assessments: Picus offers threats among which you can choose according to your specific environment and security needs, enabling you to conduct assessments that align with your organization's goals and minimize any potential risks.
Established Reputation and Reliability: Picus is an established risk-free cybersecurity solution with a track record of successfully helping organizations identify and mitigate security risks without causing any damage to production environments.
No, you can start your free trial without any payment information.
We want you to experience the full power of Picus Security Validation Platform risk-free and make an informed decision about upgrading.
