Vulnerability Prioritization Driven by Proof
Generic Scoring Alone Misses the Mark
Most organizations already use prioritization tools. But they rarely go beyond calculating severity. At best, they give you a long vulnerability list based on CVSS or EPSS.
With Picus, prioritization is based on proof:
- A “critical” vulnerability may already be blocked by your security controls.
- A “medium” vulnerability may open a path to sensitive data.
- Picus shows the difference, so you can focus where it matters.
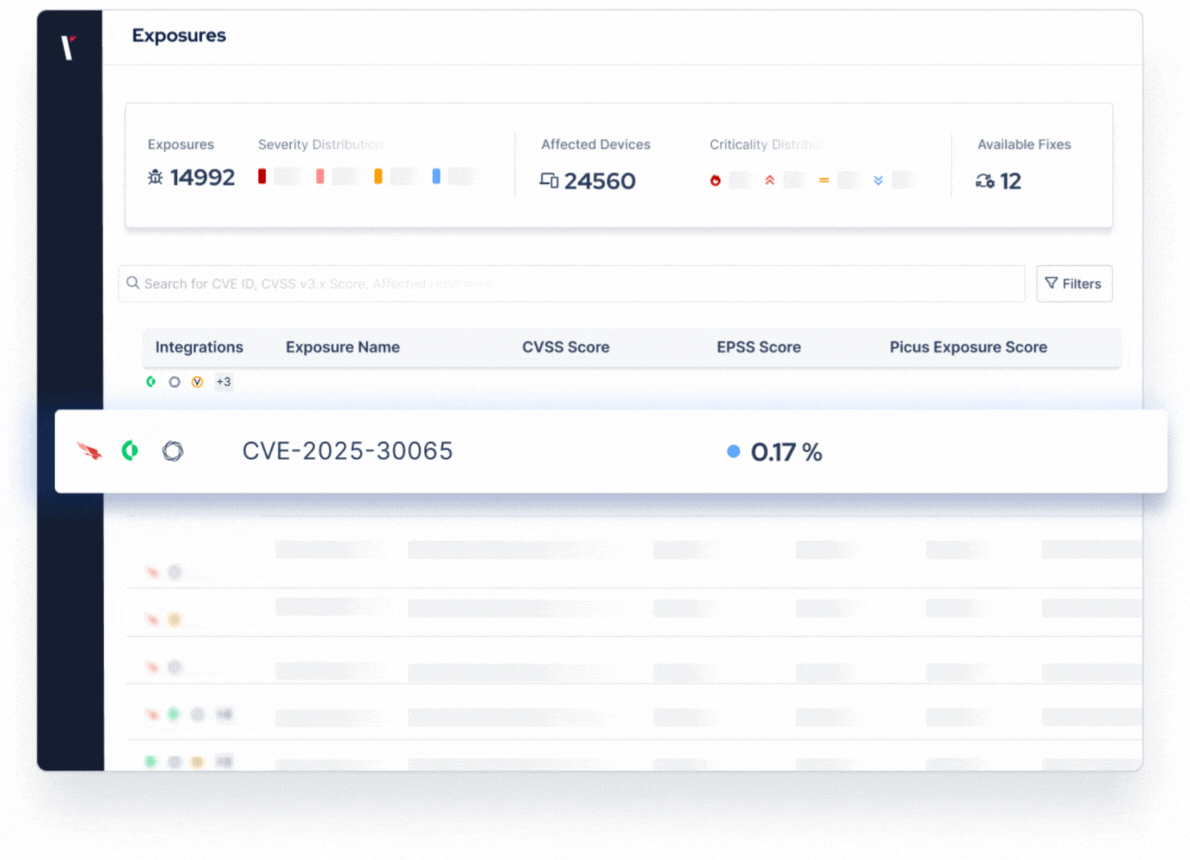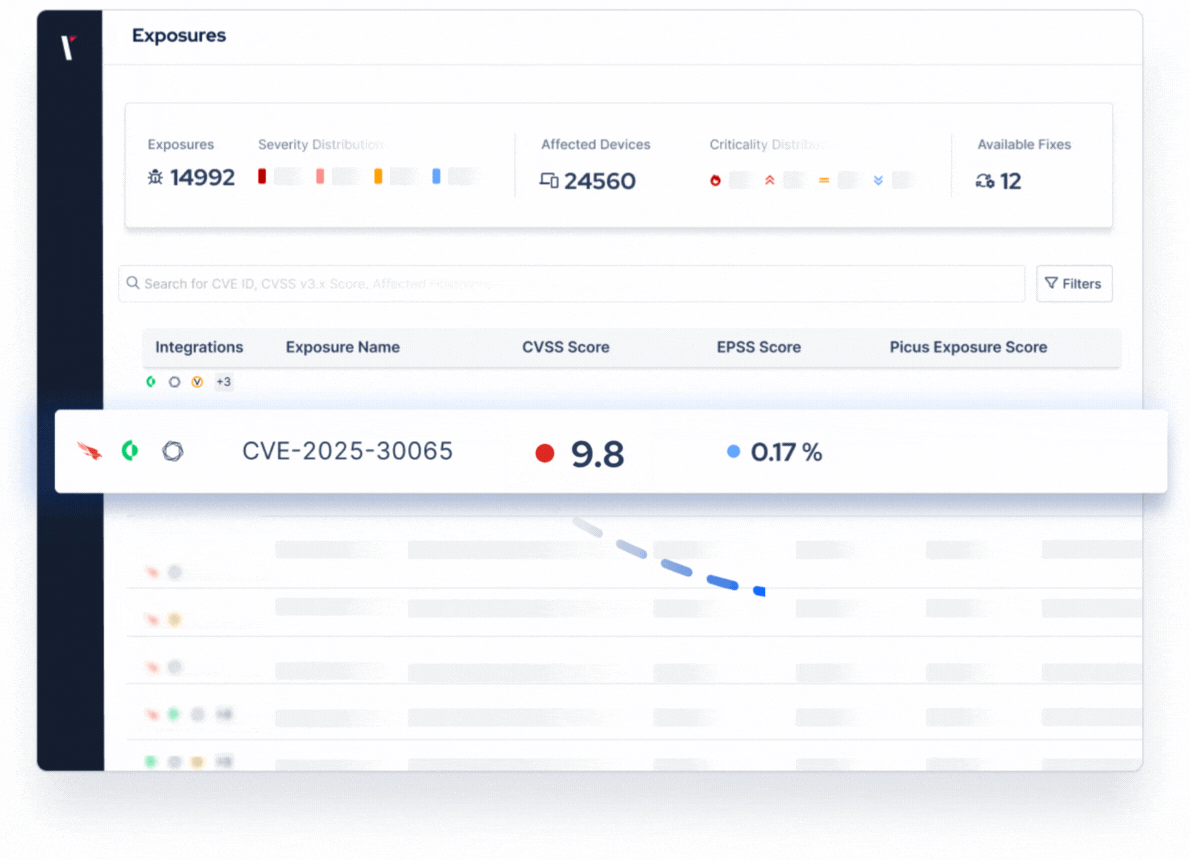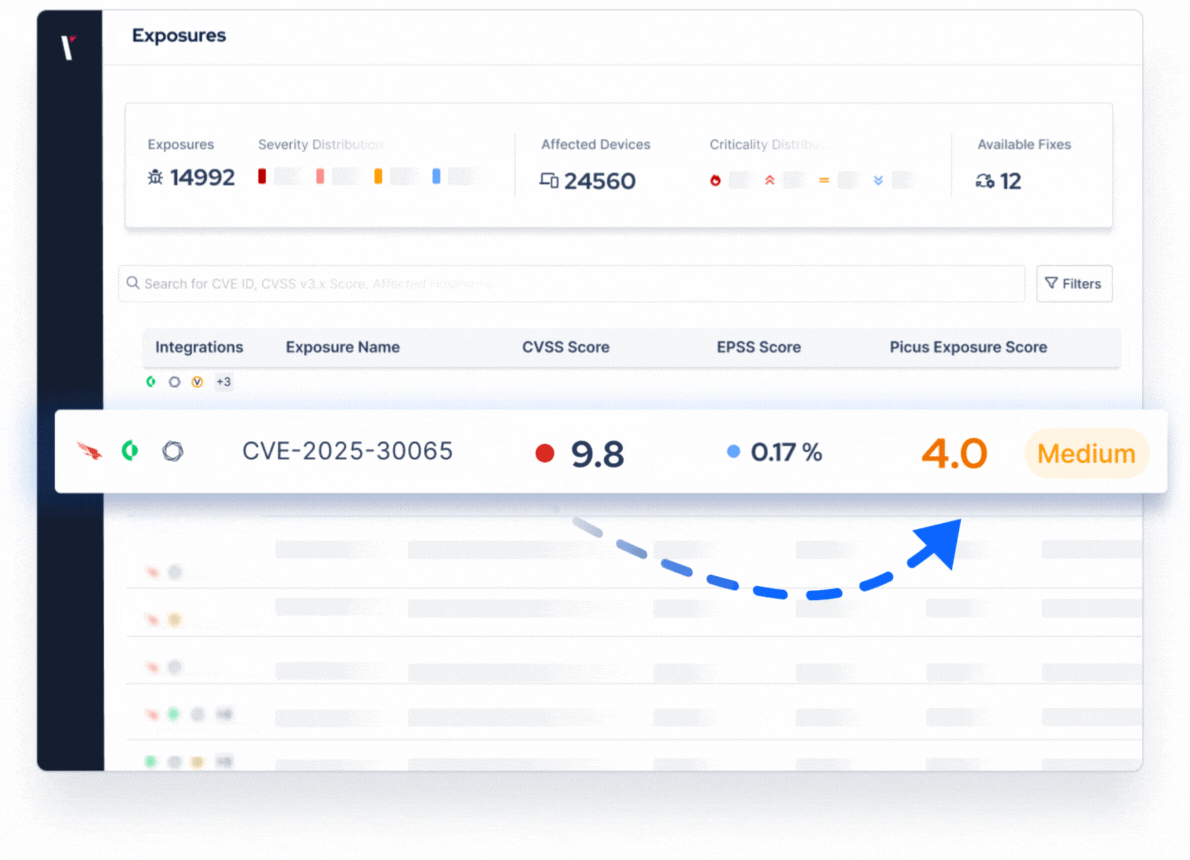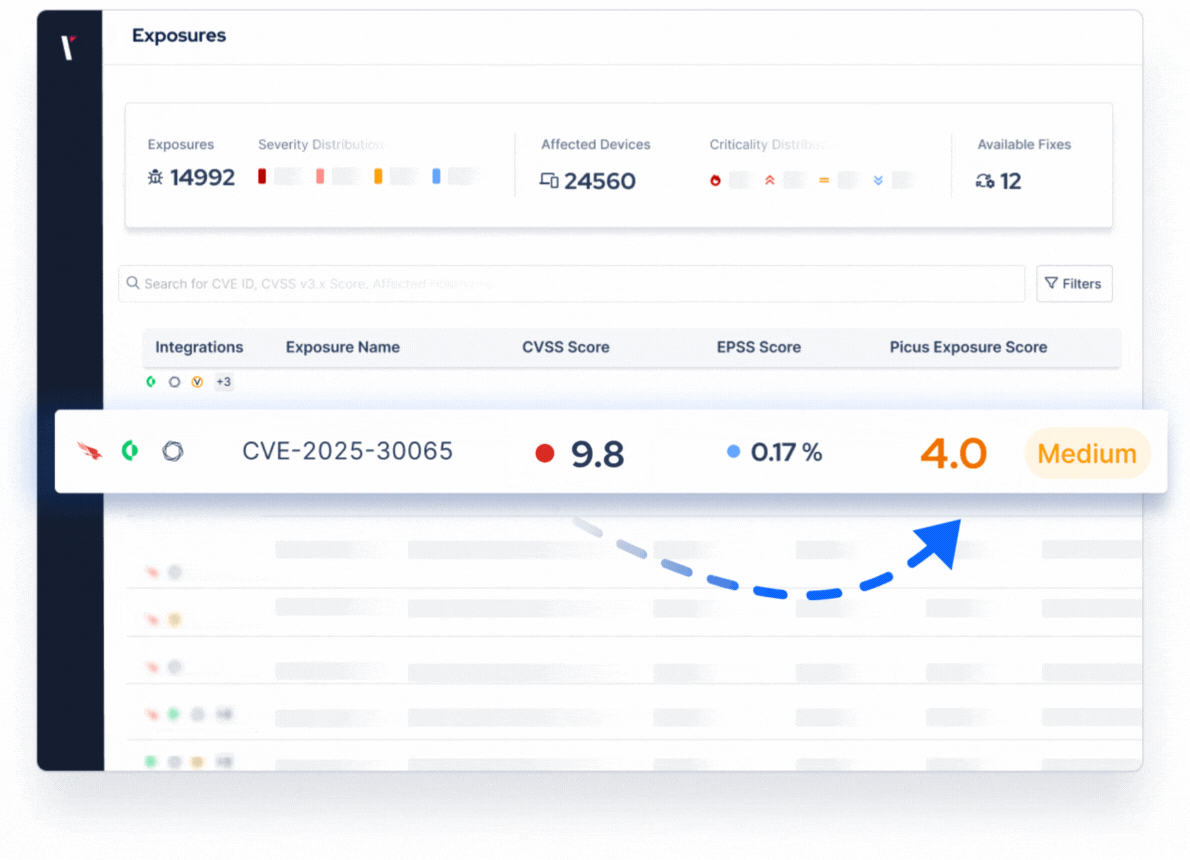
Expose Which Attacks Can Breach Your Defenses
Picus simulates the entire chain, from initial access to privilege escalation, and delivers detailed findings at every step. You see which controls stop the attack and which gaps remain.



How Picus Prioritizes Vulnerabilities
By testing vulnerabilities against your specific environment and defenses, Picus ensures that prioritization is driven by real business impact, not just CVSS scores.
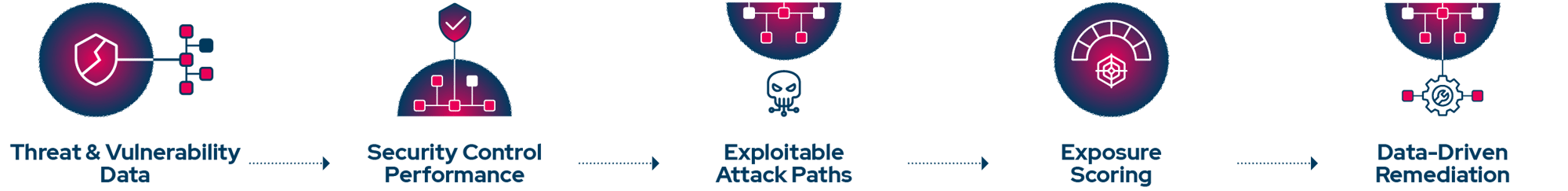
Key Capabilities
Only focus on vulnerabilities that can have an actual impact, so your team isn’t overwhelmed trying to fix everything.




Scoring That Reflects Your Reality
Security Control Performance
Factor in how effectively your defenses mitigate each vulnerability.
Asset Importance & Business Context
Adjust scores for critical systems, sensitive data, and business value.
Vulnerability Severity & Exploit Availability
Combine CVSS with EPSS, KEV, and threat intel.
Compliance Alignment
Support GDPR, NIS2, and DORA requirements with clear, risk-based prioritization.
.png?width=600&height=288&name=Score-marketing%20(1).png)
Integrations That Accelerate Action
REQUEST DEMO
Let's Chat!
Scoring alone leaves gaps.
Discover how your team can gain clarity, reduce noise, and focus on vulnerabilities that truly matter.












.png?width=353&height=200&name=Picus-BlueReport2025-Preview2-HubPage%20(2).png)